It was impossible to even imagine that a market could exist online even some years ago. In the development of technology, e-commerce is now a well established and widely accepted reality. But all good things come at a cost. In this case, it is the security threats that it may trigger. 54% of companies have experienced at least one or more successful security attacks.
60% of companies, which have received a security attack had died off/wiped off business within six months. Only 38% of global companies have handled cyber-attacks successfully. So one must have properly equipped to fight the threats. In this article, we will discuss some of the threats faced by e-commerce and how we may help.
Key Security Threats to E-Commerce—
1. Distributed Denial of Service (DDoS)
It’s normally a cyber assault undertaken by rivals to leave the network source permanently or temporarily useless for its intended users. DDoS attacks normally involve flooding the tools with bogus requests so the servers have been overloaded blocking all of the requests that are authentic. The imitation of incoming traffic flood arises from numerous hacker-controlled sources.
Thus the name Distributed Denial of Service. This trick also ensures that the attack cannot be stopped by just blocking a single source. This kind of attack is on the rise generally in the peak sales period. Such an attack can cause the loss of a lot of revenue but the biggest risk is to the reputation. Losing the trust and confidence of the customers is devastating.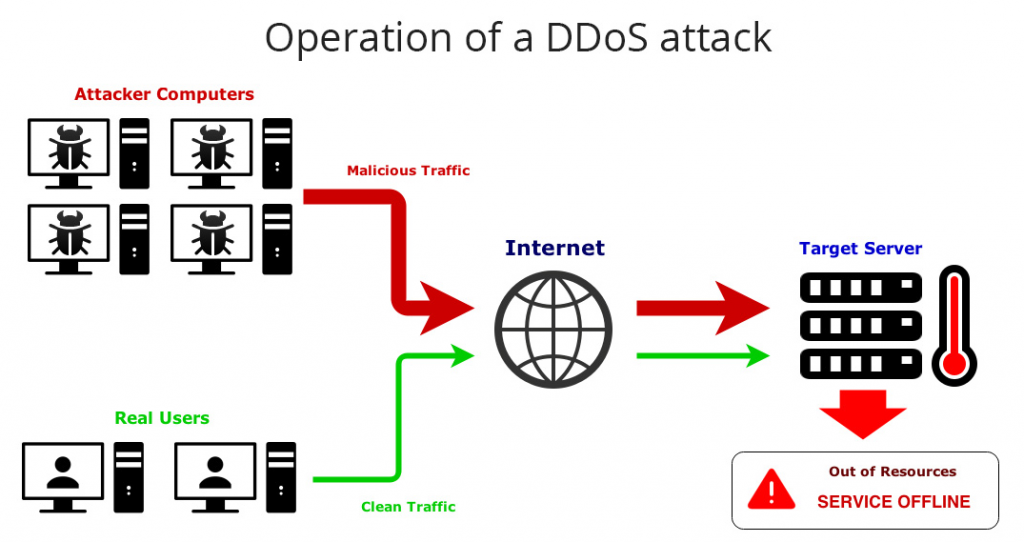
Credit card fraud is probably a classic security fraud that e-commerce sites have been facing for a very long time. It is mainly because it is quite difficult to trace. More so when your e-commerce is dealing with hundreds of transactions a day. We will try to list a few signs that may tell you that such an action is in the process :-
- If a customer’s IP address is not on the same location as the billing information of the order
- If multiple unsuccessful orders are followed by a successful one.
- An order is set to ship to another address other than the billing address.
- If you receive a sale of a much higher value than that you are used to.
In such cases verification becomes necessary before any payment is taken. Otherwise, it ultimately results in the loss of valuable inventory and paying back the customer, let alone the damaged reputation.
3. Malware
Malware is basically a kind of software to gain access to or damage a computer network developed by cyber-criminals. Through techniques like SQL injection malware files can allow hackers to
- Tamper with your database
- Gain complete access to the data in your system
- Take control of your computer and networks
- Fake your identity
- Send malicious emails on your behalf
The anti-virus protocols should be evolved to stop this.
Wikipedia defines Bots as – “a software application that runs automated tasks (scripts) over the internet. Bad bots mimic real human workflows on the web and behave like real users with the intention to cause a threat. Bots can be used in finding out stolen card numbers and also to figure out the CVVs of them using various permutation until they are successful.
A hacker can use this information to buy anything in someone else’s name. Other actions that bad bots can undertake are price scraping and account acquisition. Thankfully among various measures, there are CAPTCHAs to battle bad bots.
5. E-skimming
E-skimming is a significant risk in e-commerce. Cyber-criminals use it to steal personal data such as credit card information from the payment process pages on an e-commerce site. Misleading external links and portals to payment page can misguide shoppers.
Cyber criminals can also gain access to your site through a third-party, a successful phishing attempt or cross-site scripting. As soon as the customer accesses the payment page the payment information can be captured by the cyber criminals. Customers must have warned about such unverified websites and should be checked if they are genuine.
Author:
Ankit Pahuja is a Security Evangelist at Astra Security. Ankit was awarded for finding vulnerabilities in public networks, cameras, printers, access points & web applications for good. J Until today, he has helped 100+ businesses stay secure.
 Start using ZapInventory today
Start using ZapInventory today

